Authentication using state of user sessions and cookie session ids has been an approach that has been working for centuries. But there has been a move to develop apps with the concept of statelessness in mind with the increase of service-oriented architectures and internet facilities.
JWTs provide authentication with a stateless approach by reducing the need to monitor server meeting information. Instead, JWTs enable us to record our event information straight on the client in the type of a JWT securely and securely.
What Are JSON Web Tokens?
JWTs get a couple of criticism and skepticism, but the reality is that both session and JWT authentication have seen a majority of production usage and both implementations are safe and strong in managing user authentication. If statelessness is a practice that you value in the architecture of your system, then JWTs are right for you. In this paper, we’re going to discuss what JWTs are, the trade ups you create in selecting to use JWTs, and how you can safely execute them in your architecture.

In a Simple Way:
JSON Web Tokens (JWT) is a compact and self-contained method of transferring data safely and representing claims between participants as an object of JSON.
How Authentication works
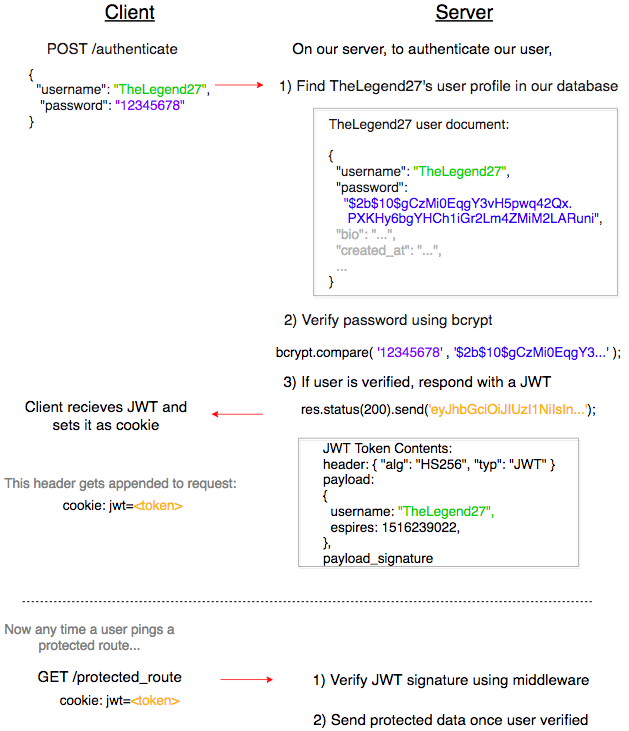
Some important point to note:
- We’re not keeping a history of database client sessions! This is the large difference between using sessions and JWT auth. In our sessionless auth architecture, we have one less data source to care about.
- Our pipeline is extremely easy! If you are simply trying to introduce authentication as logically and swiftly as feasible in your web app, then JWTs are the approach to go.
So that’s the concept behind JWTs using sessionless authentication. Now if you are familiar with authentication using sessions, this pipeline may sound similar to you. A JWT looks very similar to a cookie-specified HS256 encrypted session I d. However, JWTs are signed by request using HS256! The difference between the two is that in its payload, a JWT encodes all session data while a session I d refers to a session table.
JWTs avoid the need to monitor back-end sessions. Instead, in the JWT payload, session data is encrypted. Here the tradeoff is that the size of a JWT scale is proportional to the size of its payload. Fortunately, this is a payload that requires
|
2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 |
var express = require('express'); var jwt = require('jsonwebtoken'); var router = express.Router(); router.use(express.static(__dirname+"./public/")); if (typeof localStorage === "undefined" || localStorage === null) { const LocalStorage = require('node-localstorage').LocalStorage; localStorage = new LocalStorage('./scratch'); } function checkLogin(req,res,next){ var myToken= localStorage.getItem('myToken'); try { jwt.verify(myToken, 'loginToken'); } catch(err) { res.send ("you need login to access this page"); } next(); } router.get('/',checkLogin,function(req, res, next) { employee.exec(function(err,data){ if(err) throw err; res.render('index', { title: 'Employee Records', records:data, success:'' }); }); }); router.get('/login',function(req, res, next) { var token = jwt.sign({ foo: 'bar' }, 'loginToken'); localStorage.setItem('myToken', token); res.send("Login Successfully"); }); router.get('/logout',function(req, res, next) { localStorage.removeItem('myToken'); res.send("Logout Successfully"); }); module.exports = router; |
You can also learn more about Json Web Tokens and Node-local storage from below link:
https://www.npmjs.com/package/jsonwebtoken
https://www.npmjs.com/package/node-localstorage
Save HTML Form Record into MongoDB Database Using Express js and Mongoose js

Pradeep Maurya is the Professional Web Developer & Designer and the Founder of “Tutorials website”. He lives in Delhi and loves to be a self-dependent person. As an owner, he is trying his best to improve this platform day by day. His passion, dedication and quick decision making ability to stand apart from others. He’s an avid blogger and writes on the publications like Dzone, e27.co